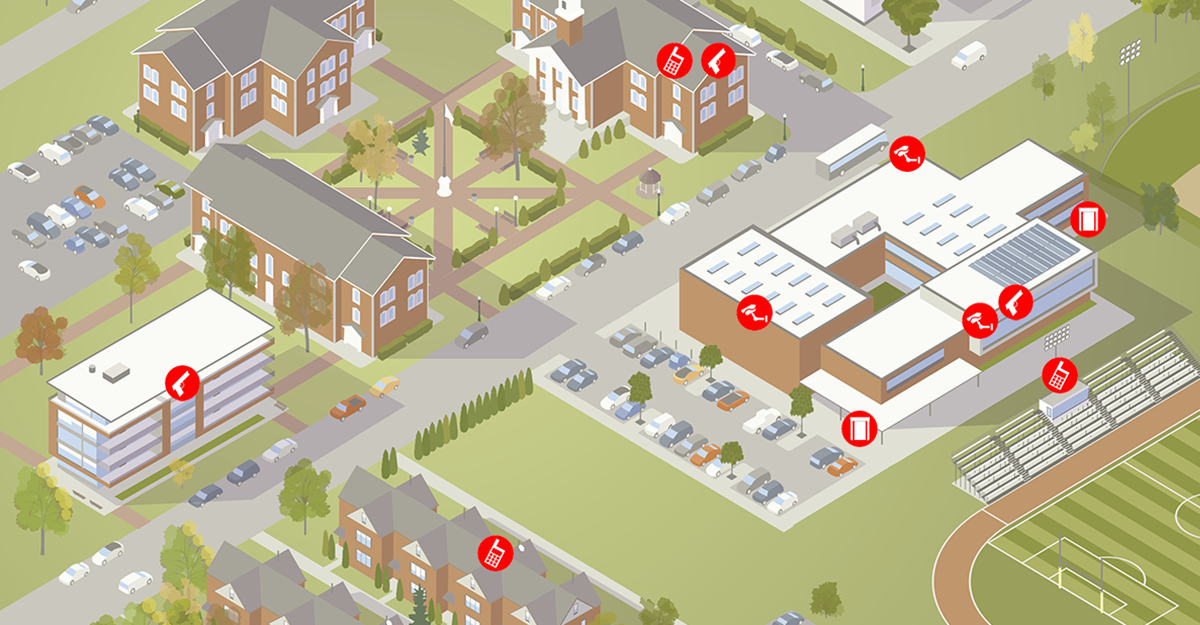
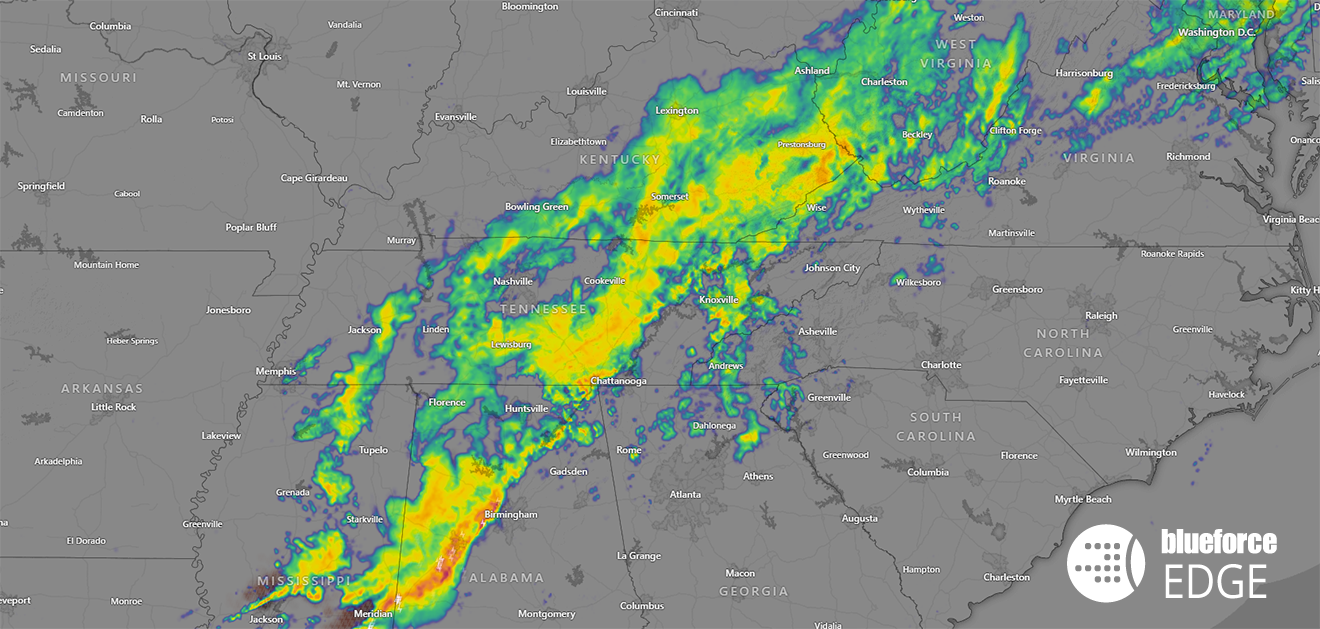
Joint All-Domain Command & Control (JADC2) is the DoD initiative to replace the current domain and control systems with one that connects the existing sensors and shooters and distribute the available data to all domains (sea, air, land, cyber, and space) and forces that are part of the U.S. military. The goal is to move to a system that connects every sensor and shooter, providing...
Read MoreThe 2022 Blueforce Texas Road Show
The 2022 Blueforce Texas Road Show gives you hands-on access to the latest in Public Safety, Safe Campus, and Autonomous Platform technologies. The Road Show kicks off Tuesday October 11, 2022 in Houston. For more information, click here…