A Most Exceptional Macy’s Thanksgiving Parade in NYC
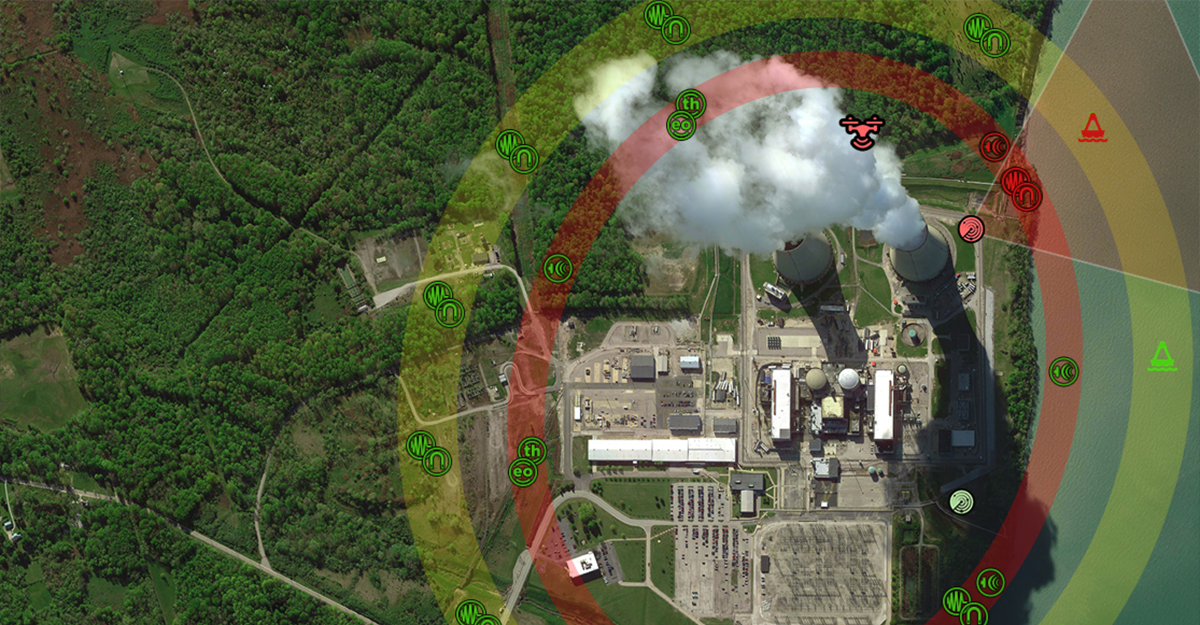
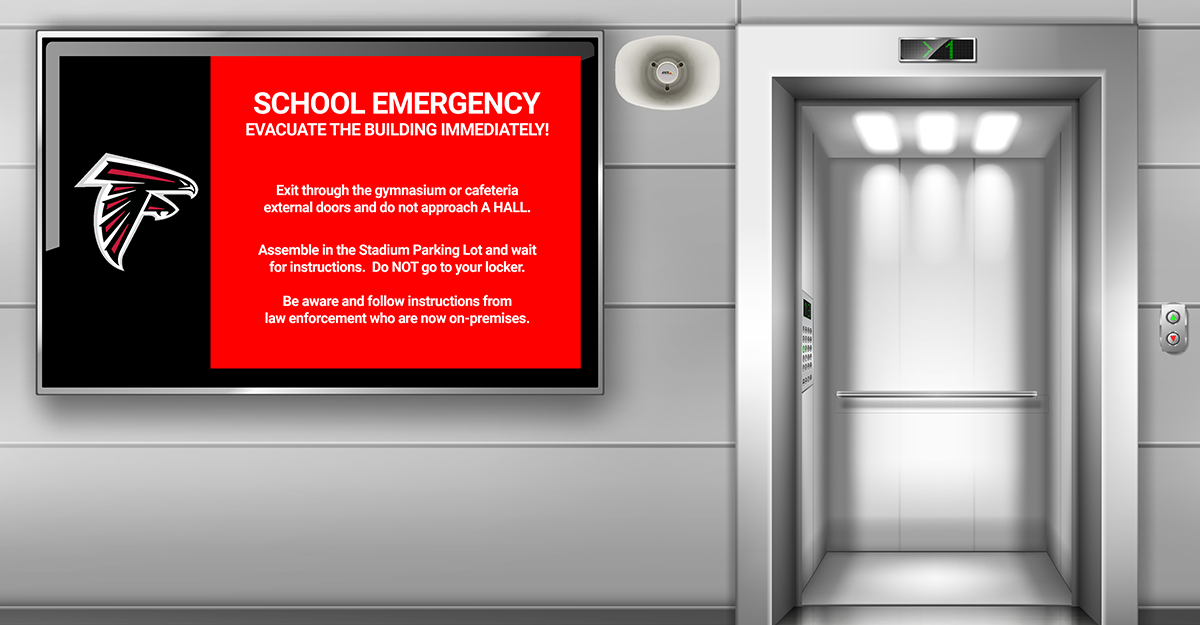
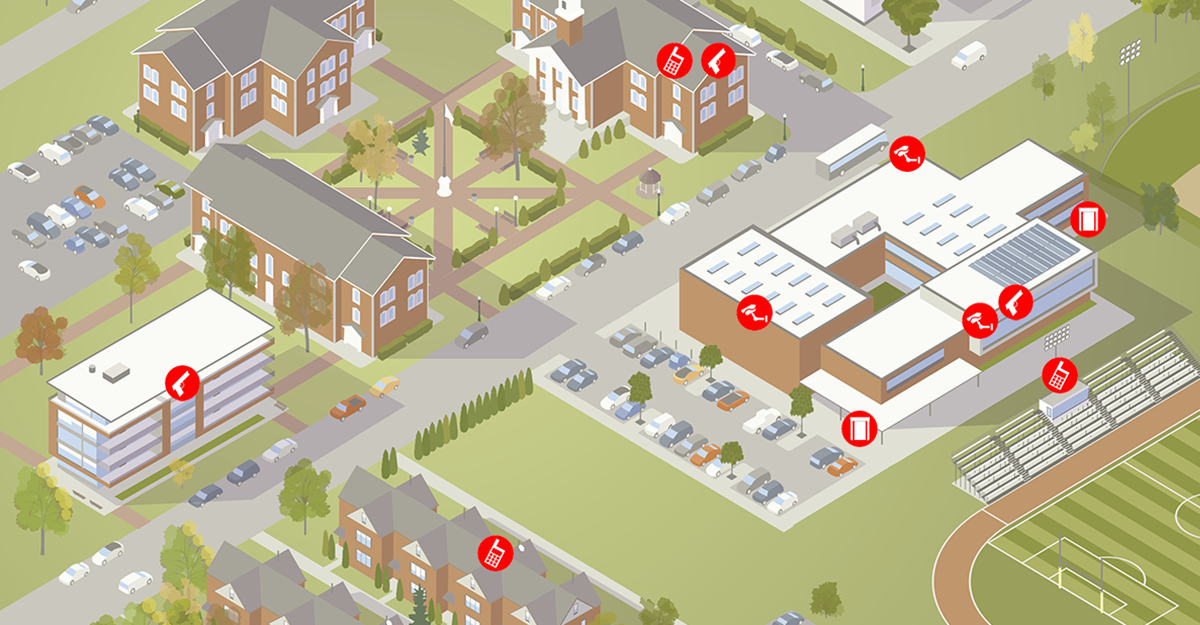
After Action Reports (AAR) may be one of the most important tools in emergency management and counter-terrorism operations. When used as a critical component of an agency's tactics, techniques, and procedures (TTP), AAR's can be an important litmus test which questions our assumptions about threats, which ultimately impacts training, mitigation, and response. Blueforce was used extensively over the entire Macys Thanksgiving Day parade route and...
Read More